With 614,000 views, the recent WUSA9 3-minute demo showing how easily someone can hijack a hotel’s Wi-Fi struck a nerve. It’s not just clickbait — it’s a warning. The tools for digital mischief have evolved. What we once shrugged off as “public Wi-Fi risk” is now a real, everyday danger.
Even places you assume are “safe” (luxury hotels, I’m looking at you) are being weaponized. That “hotel Wi-Fi login portal” you’re itching to tap into the moment you RSVP your room? Could be a trap.
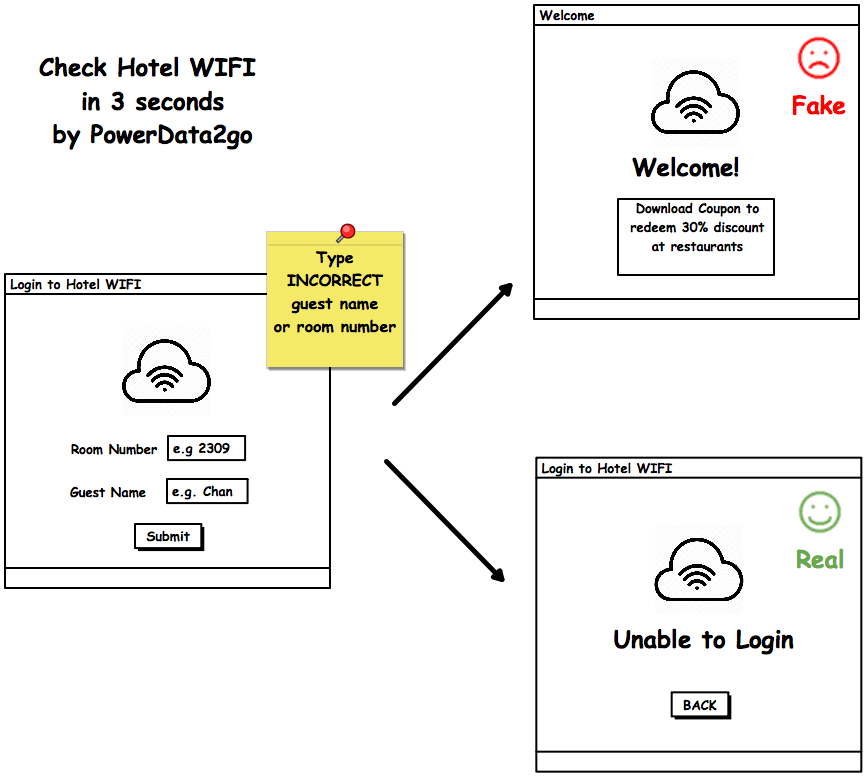
I’ve connected to over 400 hotel Wi-Fi networks during work and play. Even with all my nerdy precautions, I still treat logging into a new network like stepping off a cliff. If I sat down to do a full-blown security audit (like I did back in my Verizon security team days) every time — I’d have zero time left to actually use the internet.
So instead, I distilled a 3-second “sanity check” that (so far) keeps me from feeding data to hackers:
Type an obviously wrong username and password.
If the login still works, it’s not your hotel network — it’s a fake Wi-Fi portal. Disconnect immediately and alert front desk or IT.
Here’s the reasoning: a real hotel system expects valid credentials (room number, last name, etc.). A hacker’s spoofed portal can’t know those ahead of time — so it often “accepts” anything you throw at it.
These are not exotic hacks — they’re copy-paste tactics that prey on human trust. Add in stories like Russian spies setting up surveillance vans outside hotels to intercept Wi-Fi traffic, and you realize: this isn’t paranoia, it’s smart.
Stay sharp. Use that 3-second test. Never assume “hotel Wi-Fi = safe.” Don’t be a victim of the “evil twin” Wi-Fi trick.
Have a great week ahead.
Based in Singapore, PowerData2Go's solution is a blend of personal WIFI hotspot hardware and VoIP (voice over IP) software working together to bring seamless connectivity to frequent travelers.